Hackers offer an IoT botnet for $7,500
The recent attack may have been just a test. Security firm RSA reports discovering in October that hackers are offering access to a massive IoT botnet in a criminal underground forum.
A massive DDoS attack last week against the DynDNS service, one of the largest Domain Name Systems (DNS), caused a widespread failure of the internet. A large proportion of Internet users could not reach important Internet services. Sites like Twitter, GitHub, PayPal, Amazon, Reddit, Netflix, and Spotify have been inaccessible to netizens in the US.
The Dyn DNS service has been inundated by a cataclysmic wave of requests originating from millions of vulnerable IoT devices. Dyn announced that a large number of hijacked Internet of Things devices were being used by attackers to fuel the massive DDoS attack.
“Flashpoint confirmed that parts of the infrastructure were responsible for the Distributed Denial-of-Service (DDoS) attack against DynDNS botnets compressed by the Mirai malware. Mirai botnets were most recently used as a DDoS attack against the blog “Krebs On Security” by security researcher Brian Krebs and French Internet service provider OVH.” according to the analysis published by Flashpoint. “The Mirai malware aims to take over Internet of Things (IoT) devices such as routers, digital hard disk recorders (DVRs), and webcams/security cameras and consolidate a large number of these devices into a botnet, which is then used for the DDoS attack
The following are the key discoveries of the Report published by Flashpoint:
Flashpoint confirmed that parts of the infrastructure were responsible for the distributed denial-of-service (DDoS) attack against DynDNS botnets, which compressed by the Mirai malware.
Mirai botnets were most recently used as a DDoS attack against the Krebs On Security blog and OVH.
As of 5:30pm EST, attacks against DynDNS continue. Flashpoint is coordinating with numerous vendors and law enforcement agencies to track infected devices to substantiate that the botnet was used for the attacks.
This is not surprising when you compare the prices with the operating costs.
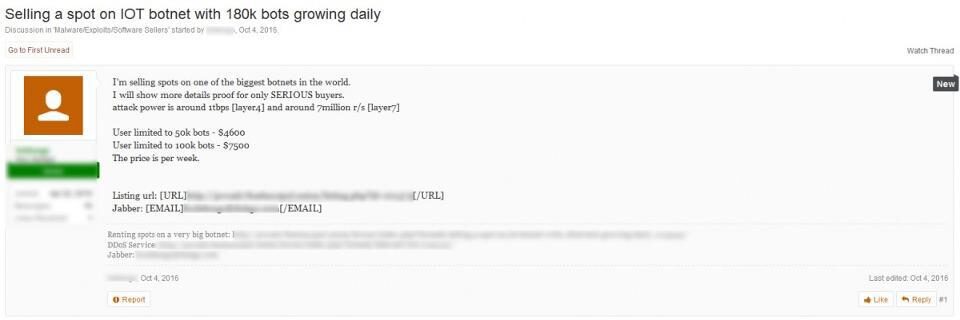
Security firm RSA revealed in October that it discovered hackers offering access to a massive IoT botnet in a criminal underground forum.
This is the first time we Have seen an IoT botnet for sale or rent. Especially one that has this attack power. The growing DDoS opportunities are certainly a worrying trend.
Daniel Cohen, Chair of the FraudAction business unit at RSA Forbes
According to RSA, hackers offered an IoT botnet capable of performing attacks with 1Tbps of traffic. The same volume of traffic was used against French provider OVH. It is unclear whether the botnet consisted of devices infected with Mirai malware.
The hackers offered a botnet consisting of 50,000 devices for $4,600. 100,000 bots now cost $7,500.
“Hackers have been selling access to botnets for a long time, but until now they have not allowed the use of IoT devices such as connected cameras, refrigerators and household appliances explicitly advertised. The infamous Lizard Squad accumulated significant botnets for their LizardStresser “booter” – a rental DDoS weapon – mainly endangering vulnerable routers,” FORBES reported.
IoT providers are slowly becoming aware of the risks posed by cyber attacks. Xiongmai Technology (XM), for example, the Chinese maker of surveillance and home video devices threatened by the Mirai botnet, recently released a patch to prevent devices from being infiltrated.
However, any devices with firmware released prior to September 2015 and using the default username and password remain vulnerable via telnet.
Attacks powered by the IoT botnet like Friday’s are difficult to prevent. Using a secondary or backup DNS provider could make it more difficult for attackers to shut down the web service.
For more countermeasures, visit the FORBES Blog Post.